SQL Injection

SQL injection is a web security vulnerability that allows an attacker to execute malicious SQL statements against a database. This can be done by including special characters in a web form input field, which are then passed to the database as part of an SQL query. If the input is not properly sanitized, the attacker can use this to bypass authentication, access sensitive data, or even modify the database.
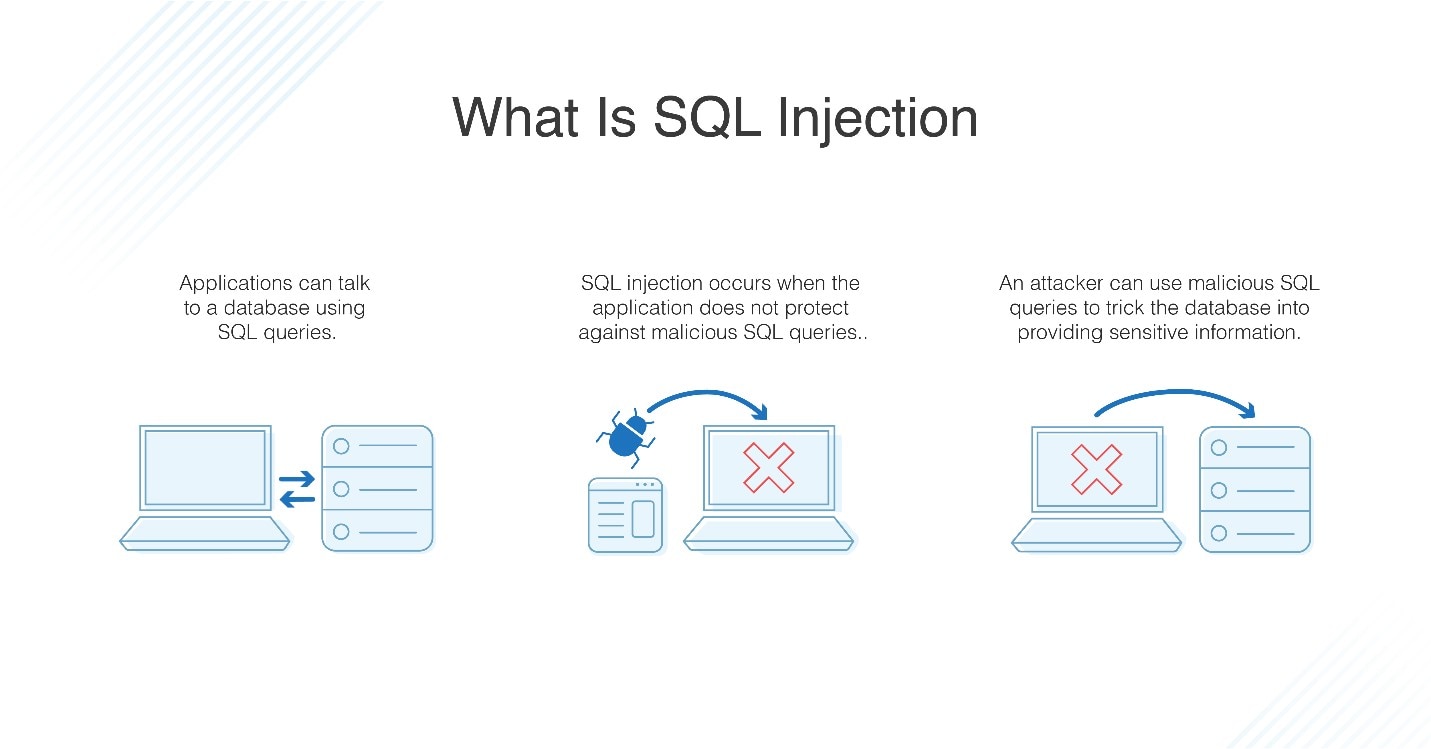
How SQL Injection Works

SQL injection attacks work by exploiting the fact that SQL queries are constructed dynamically based on user input. When a user enters data into a web form, that data is typically passed to the database as part of an SQL query. If the input is not properly sanitized, the attacker can include special characters that will cause the query to be executed in a way that the attacker intended.
For example, consider the following SQL query:
SELECT * FROM users WHERE username = 'admin' AND password = 'password';This query will return all rows from the users table where the username is ‘admin’ and the password is ‘password’. If the attacker can modify the input, they can change the query to the following:
SELECT * FROM users WHERE username = 'admin' OR '1'='1';This query will always return all rows from the users table, because the condition '1'='1' is always true. This allows the attacker to bypass authentication and access all user records.
Preventing SQL Injection
There are several ways to prevent SQL injection attacks. The most important is to properly sanitize user input. This can be done by using a library or framework that automatically removes special characters from input. It is also important to use parameterized queries, which prevent attackers from inserting malicious code into SQL queries.
Here are some additional tips for preventing SQL injection attacks:
- Use strong passwords for database accounts.
- Keep your software up to date.
- Use a web application firewall (WAF).
- Educate your users about the risks of SQL injection.
