Vulnerability Testing in Malaysia
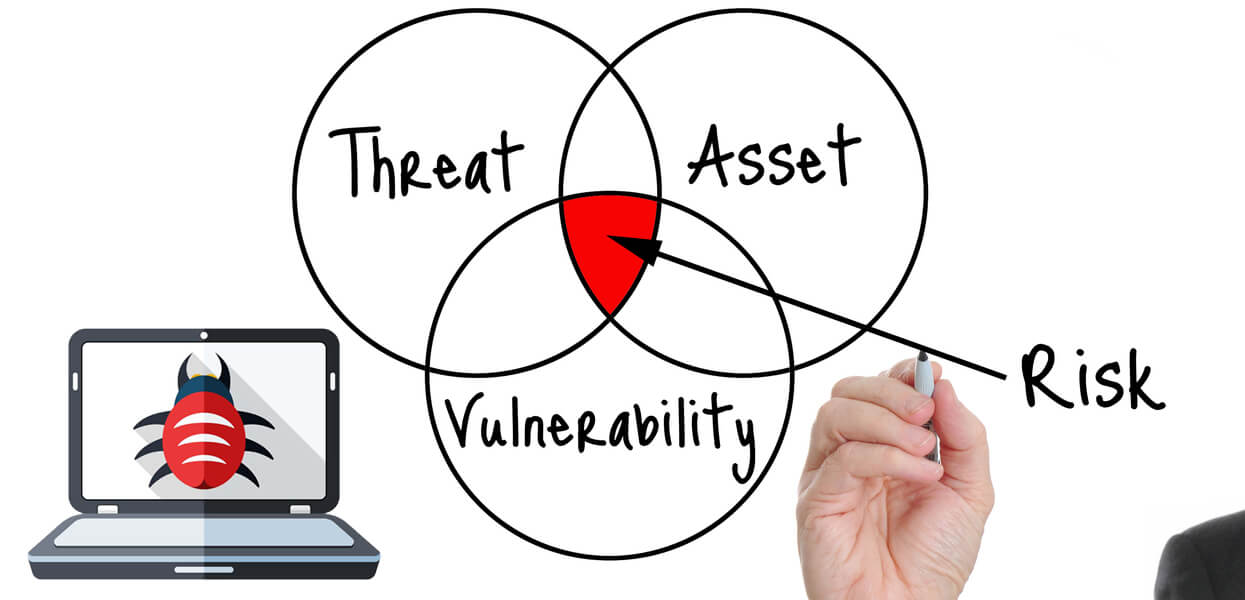
Vulnerability testing is a critical aspect of cybersecurity that helps organizations identify, assess, and mitigate security vulnerabilities in their systems and networks. In Malaysia, vulnerability testing is becoming increasingly important as businesses face growing threats from cyberattacks.
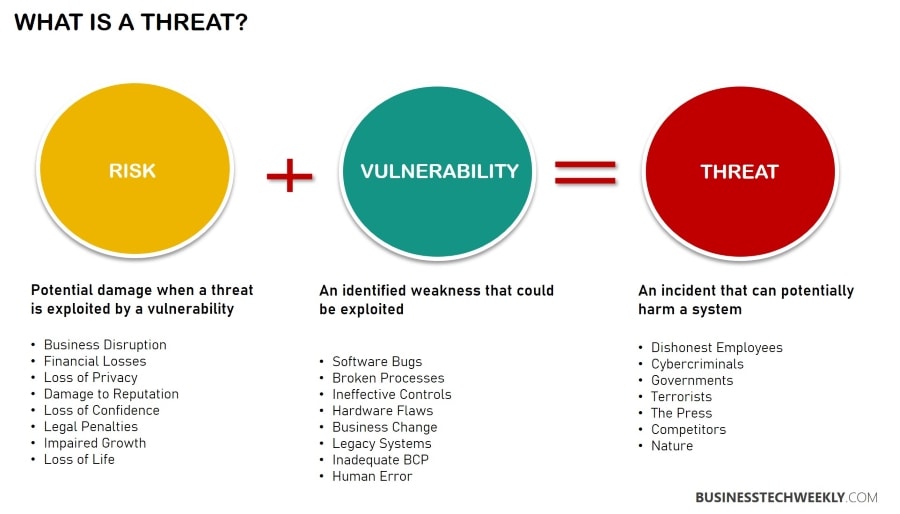
Types of Vulnerability Tests
There are various types of vulnerability tests, each with its own purpose:
- External Vulnerability Scan: Scans systems from the outside perspective of an attacker to identify potential entry points into the network.
- Internal Vulnerability Scan: Examines systems from the inside to detect vulnerabilities that could be exploited by insiders or malicious software.
- Network Vulnerability Assessment: Tests the security of network devices, such as routers and switches, for misconfigurations or vulnerabilities.
- Web Application Vulnerability Assessment: Scans web applications for vulnerabilities that could allow attackers to compromise data or gain unauthorized access.
Benefits of Vulnerability Testing
Vulnerability testing offers numerous benefits:
- Reduced Risk: Identifies vulnerabilities before they can be exploited by attackers, reducing the risk of security breaches and data loss.
- Improved Security Posture: Strengthens the security of systems and networks, making them less susceptible to cyberattacks.
- Compliance: Helps organizations comply with industry regulations and standards, such as PCI DSS and HIPAA, which require regular vulnerability assessments.
- Enhanced Awareness: Provides a clear understanding of potential vulnerabilities, enabling organizations to make informed decisions about security investments.
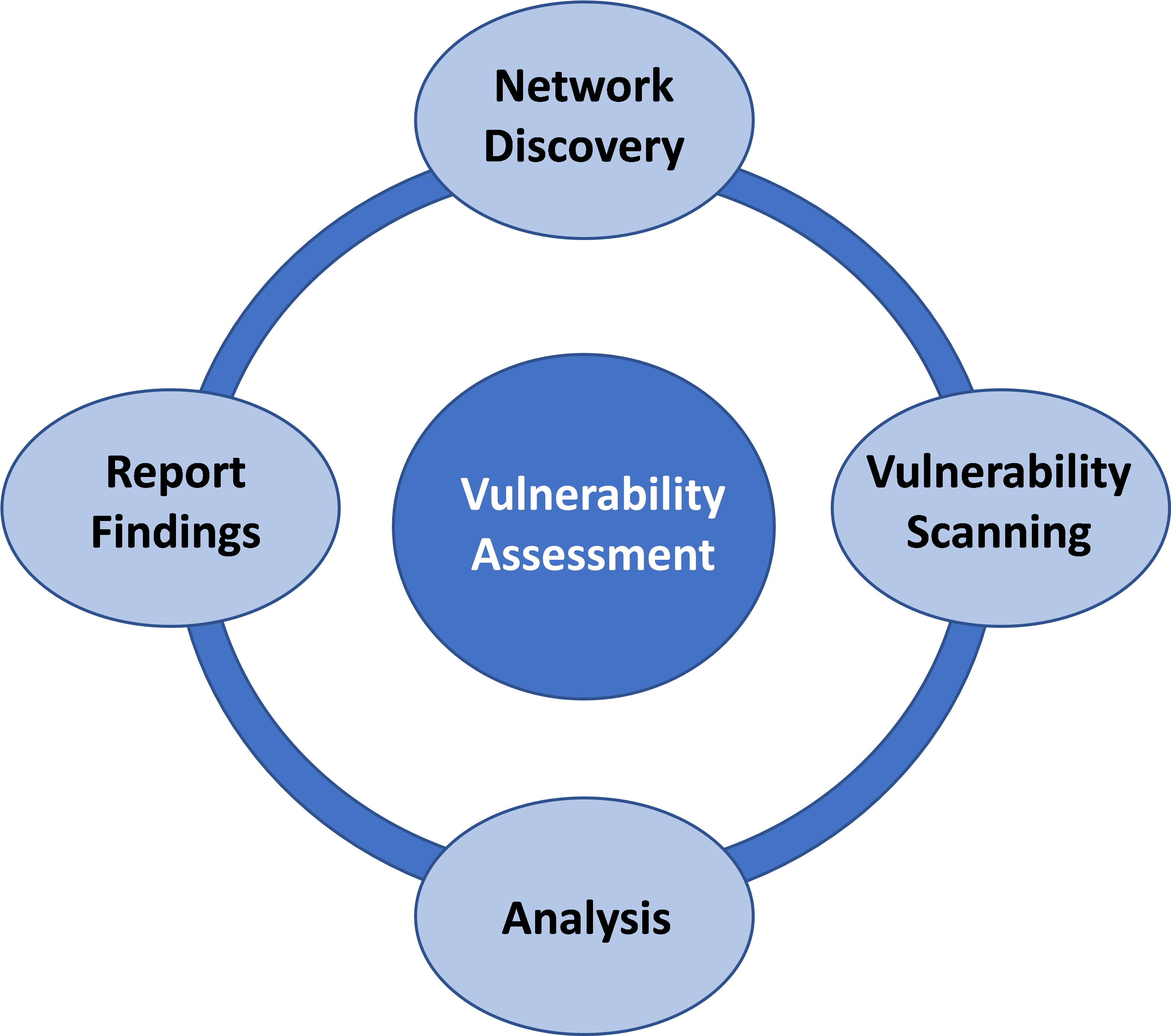
Vulnerability Testing Process
In Malaysia, vulnerability testing typically follows a structured process:
- Planning: Define the scope of the test, identify the assets to be assessed, and select the appropriate testing tools.
- Scanning: Utilize automated or manual tools to scan systems and networks for vulnerabilities.
- Analysis: Review scan results to identify valid vulnerabilities, prioritize them based on risk, and assess the potential impact of each vulnerability.
- Reporting: Generate a comprehensive report outlining the findings, including vulnerability details, recommendations, and mitigation plans.
- Remediation: Implement necessary measures to mitigate identified vulnerabilities, such as patching software, configuring security settings, or isolating compromised systems.
Choosing a Vulnerability Testing Provider
When selecting a vulnerability testing provider in Malaysia, consider the following factors:
- Expertise and Experience: Select a provider with a proven track record in vulnerability testing and security consulting.
- Compliance and Certifications: Ensure the provider is certified by recognized industry standards (e.g., CREST, OSCP).
- Technology and Tools: Choose a provider that utilizes advanced scanning technologies and tools for comprehensive vulnerability assessments.
- Support and Communication: Look for a provider that offers responsive support and clear communication throughout the testing process.
Vulnerability testing is essential for organizations in Malaysia to protect their systems and data from cyberattacks. By partnering with a reputable vulnerability testing provider, businesses can identify and mitigate vulnerabilities effectively, enhancing their overall security posture.
