Vulnerability Test Hong Kong

A vulnerability test, also known as a vulnerability assessment or penetration test, is a simulated cyberattack that evaluates the security of a computer system, application, or network. The goal is to identify vulnerabilities that could be exploited by an attacker to gain access to sensitive data, disrupt operations, or cause financial damage.
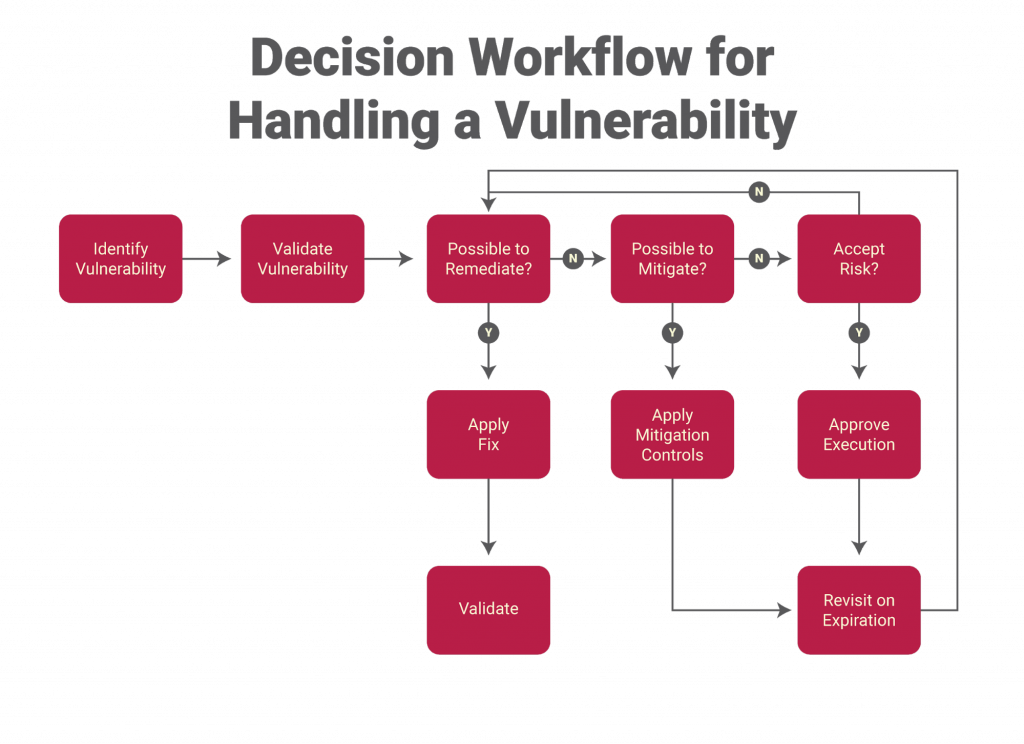
Vulnerability tests are an essential part of any comprehensive cybersecurity strategy. They help organizations to understand their security risks and take steps to mitigate them. A well-conducted vulnerability test can provide valuable insights into the security posture of an organization and help to prioritize remediation efforts.
There are a number of different types of vulnerability tests that can be performed. Some of the most common include:
- Network vulnerability tests: These tests assess the security of a network by scanning for vulnerabilities in network devices, such as routers, switches, and firewalls.
- Application vulnerability tests: These tests assess the security of applications by scanning for vulnerabilities in the code.
- Database vulnerability tests: These tests assess the security of databases by scanning for vulnerabilities in the database software and configuration.
- Web application vulnerability tests: These tests assess the security of web applications by scanning for vulnerabilities in the code and configuration.
The scope of a vulnerability test can vary depending on the needs of the organization. A comprehensive vulnerability test will typically include all of the types of tests listed above. However, a more limited test may be sufficient for organizations with a smaller security budget or a lower risk profile.
Vulnerability tests can be performed by internal IT staff or by external security consultants. External consultants often have more experience and expertise in vulnerability testing and can provide a more objective assessment of an organization’s security posture.
The results of a vulnerability test are typically presented in a report that identifies the vulnerabilities that were found, along with a severity rating for each vulnerability. The severity rating is based on the potential impact of the vulnerability and the likelihood of it being exploited.
Organizations can use the results of a vulnerability test to prioritize their remediation efforts. The most critical vulnerabilities should be fixed immediately, while less critical vulnerabilities can be fixed over time.
Vulnerability tests are an essential part of any comprehensive cybersecurity strategy. They help organizations to understand their security risks and take steps to mitigate them. A well-conducted vulnerability test can provide valuable insights into the security posture of an organization and help to prioritize remediation efforts.## Vulnerability Test Hong Kong
Executive Summary
Vulnerability testing is a critical aspect of maintaining a secure IT infrastructure. By identifying and addressing vulnerabilities, organizations can significantly reduce their risk of cyberattacks and data breaches. In Hong Kong, where the threat landscape is constantly evolving, vulnerability testing is more important than ever. This article provides a comprehensive guide to vulnerability testing, including its benefits, methodologies, and best practices.
Introduction
Vulnerability testing is the process of identifying, quantifying, and prioritizing vulnerabilities in an IT system. It involves simulating attacks to determine whether a system is vulnerable to known or potential threats. By understanding the vulnerabilities present in a system, organizations can take steps to mitigate or eliminate them, reducing their risk of being compromised.
FAQs
1. What are the benefits of vulnerability testing?
Vulnerability testing provides numerous benefits, including:
- Identification of vulnerabilities that could be exploited by attackers
- Prioritization of vulnerabilities based on their risk level
- Validation of security controls and mitigation strategies
- Improvement of security posture and reduction of risk
2. What are the different types of vulnerability tests?
There are various types of vulnerability tests, such as:
- Network vulnerability scans
- Web application vulnerability scans
- Database vulnerability scans
- Wireless vulnerability scans
- Physical security vulnerability assessments
3. How often should vulnerability testing be performed?
The frequency of vulnerability testing depends on several factors, including:
- The criticality of the IT system
- The rate at which new vulnerabilities are discovered
- The regulatory compliance requirements
Top 5 Subtopics:
1. Vulnerability Assessment Tools
- Types of tools: Automated scanners, manual testing tools, hybrid solutions
- Features to consider: Accuracy, speed, coverage, ease of use
- Cloud-based tools: Integration with cloud platforms, scalability, cost-effectiveness
- Open-source tools: Free to use, community support
- Commercial tools: Advanced features, technical support
2. Vulnerability Management Process
- Identification: Identifying vulnerabilities through testing and assessment
- Assessment: Evaluating vulnerabilities based on risk level
- Prioritization: Determining which vulnerabilities to address first
- Remediation: Mitigating or eliminating vulnerabilities
- Reporting: Documenting vulnerability findings and remediation actions
3. Risk Assessment and Prioritization Techniques
- CVSS scoring: Assigning severity scores to vulnerabilities
- Attack likelihood and impact analysis: Estimating the probability of an attack and its potential consequences
- Business impact analysis: Determining the impact of a vulnerability on business operations
- Threat intelligence: Incorporating threat information to prioritize vulnerabilities
- Regulatory compliance: Identifying vulnerabilities that violate industry regulations or standards
4. Reporting and Communication
- Clear and concise reporting: Presenting vulnerability findings in an easily understandable manner
- Executive summaries: Providing a high-level overview of the results
- Technical details: Describing vulnerabilities and remediation actions in technical terms
- Communication channels: Email, ticketing systems, reports
- Stakeholder involvement: Ensuring that all stakeholders are aware of vulnerability findings
5. Continuous Monitoring and Penetration Testing
- Continuous monitoring: Regular scanning for vulnerabilities
- Penetration testing: Simulated attacks to test the effectiveness of security measures
- Vulnerability management platforms: Providing automated vulnerability detection and tracking
- Managed security services: Outsourcing vulnerability testing and management to specialized providers
- Red team assessments: Independent security testing to identify and exploit vulnerabilities
Conclusion
Vulnerability testing is a vital component of a comprehensive cybersecurity strategy. By regularly identifying and addressing vulnerabilities, organizations can significantly reduce their risk of cyberattacks and data breaches. With the rapidly evolving threat landscape, it is essential to stay proactive and leverage the latest technologies and best practices in vulnerability testing. By following the guidance outlined in this article, organizations in Hong Kong can ensure the security and resilience of their IT infrastructure.
Keyword Tags:
- Vulnerability testing Hong Kong
- Vulnerability assessment
- Vulnerability management
- Risk assessment and prioritization
- Cybersecurity
